Email Investigations and Digital Forensics
- Sep 02, 2023
- Outlook»Email Viewer
Email is the most commonly used form of communication among businesses entities or individuals, and it is often exposed to illegitimate uses. If you are a forensic investigator, you are probably need to be able to determine if an email has or has not been falsified (email spoofing), recognize a malware email attachment and phishing. This article will explore a few basic methods on how to gather and analyze data related to an email investigation and forensic analysis.
Email Headers and MAPI properties
The first steps in any email investigation are to identify all the potential sources of information. The email header include a lot of fields (MAPI properties). The most known properties are To, From, Received, Body and the Subject. But there are a lot of other, more obscure properties that aren’t shown in Outlook or Gmail.
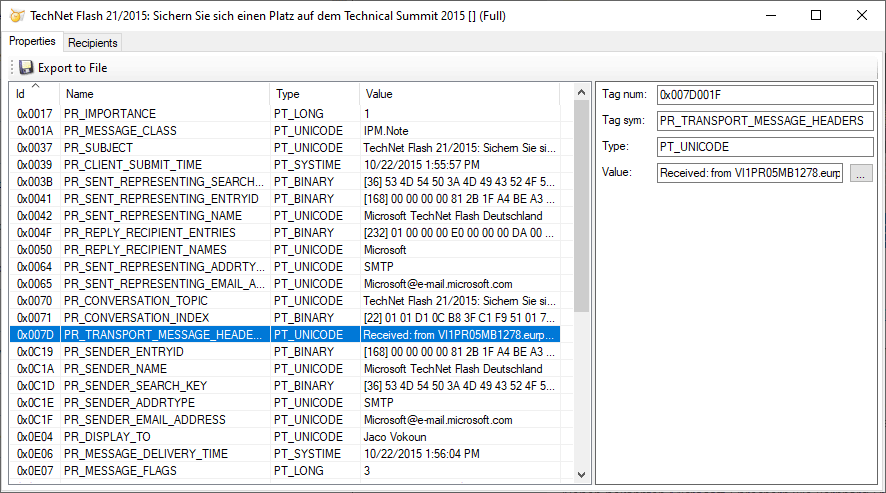
For instance, PR_TRANSPORT_MESSAGE_HEADERS (0x007D) property contains what is essentially a tracking log for the email, recording the path it took from the sender’s email service to the service hosting your own email.
Email authentication
Is the email legit? Authenticating DKIM and ARC signatures, we can have confidence that it really is from who it says it’s from. While a validated DKIM signature guarantees that you have the same email that was sent; a validated ARC signature can guarantee that you have the same email that was received by the receiving server.
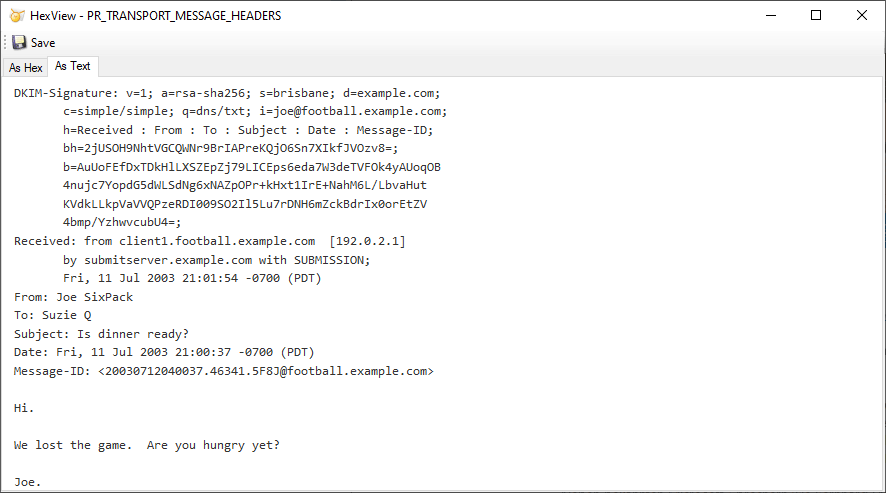
Remember, DKIM is meant to be used when the email was received right away, not months or years later.
Email Body
Email can be sent in several formats: plain text, RTF and HTML. You could test them to see if they matched. Both RTF and HTML formats use formatting codes. Using these formatting codes we did a low-level analysis of the body text.
Email Date and Time
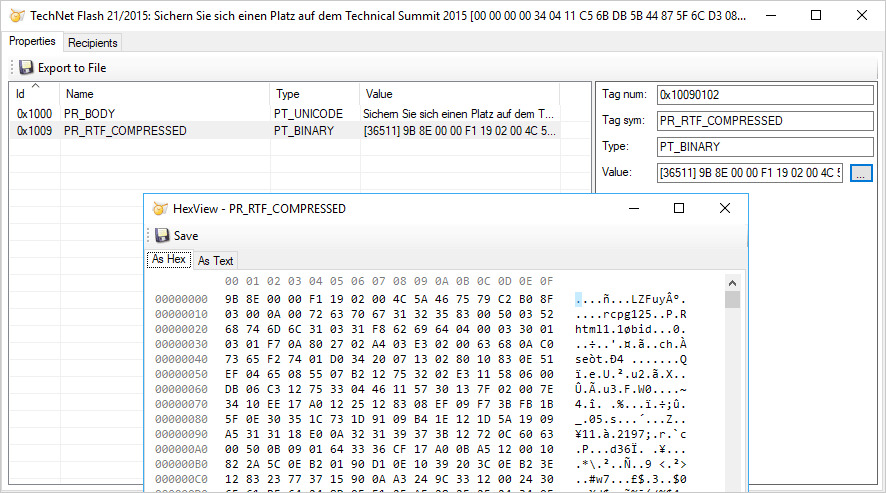
At the time a sender submits an e-mail, it gets stamped with the date and time in the PR_CLIENT_SUBMIT_TIME property. When that e-mail reaches the recipient’s mailbox, Outlook/Exchange stamps the PR_MESSAGE_DELIVERY_TIME and PR_CREATION_TIME properties. If the e-mail remains unaltered, the PR_LAST_MODIFICATION_TIME will match the PR_CREATION_TIME property. Obviously if these two properties do not match, it means the e-mail was modified by the user as no other process will update this property.
Conversation Index
The email conversation index property indicates the relative position of a message within a conversation thread and is typically populated by the e-mail client for each outgoing message. Information extracted from the Conversation index property can help answer key questions such as:
- Is the message in question a new message, or was it created by replying to or forwarding another message?
- If the message is part of an e-mail thread, when was the thread started?
- When were other messages in the e-mail thread created?
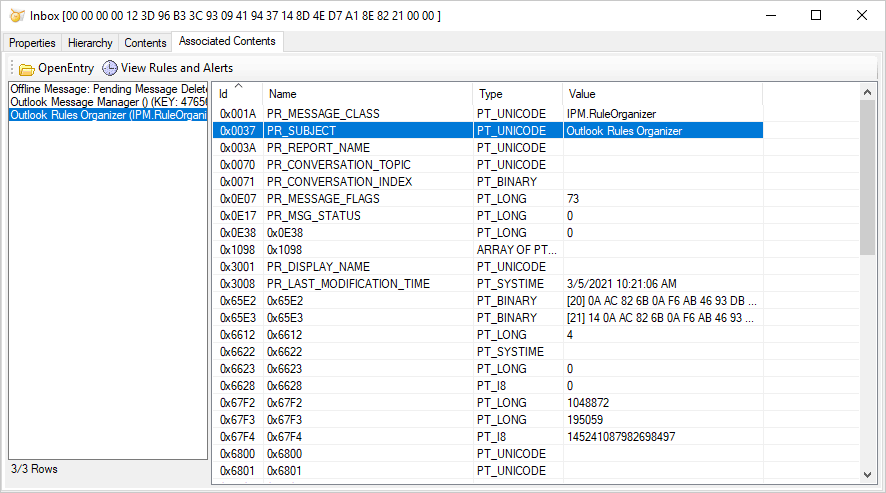
Hidden Inbox Rules and Alerts
The hidden rules may contains a sensitive information, but are no longer visible in Outlook. Since Outlook 2010, rules are stored on a per mailbox basis. If user has configured multiple mailboxes in Outlook, you’ll need to review the rules for each mailbox.
Conclusion
Combined with additional evidence from the email server or internal email metadata, the information contained in the email MAPI properties can be very helpful in the forensic analysis of emails.
See Also
Recover disappeared Rules and Alerts in Outlook
Find hidden Outlook Rules and Alerts. Create a backup copy of your rules by exporting rules to a .rwz file. Import Rules and Alerts. Supports corrupt, orphan, protected .pst and .ost files.
Emails disappearing from Outlook inbox
Emails may disappear when you accidentally delete or archive items in Outlook. This can also occur as a result of incorrect settings, rules, and filters. This blog provides solutions to help you recover the missing emails and restore them to your Outlook Inbox folder.